CryptoLocker Virus is typically propagated as an attachment to a seemingly innocuous e-mail message, which appears to have been sent by a legitimate company or known user.
Recently we have noted infections also come in via a download from a web page. This may be a link from a spam Email or a link on a page you are browsing.
Typical Email infections may come in the following forms:-
A ZIP file attached to an email message contains an executable file with the filename and the icon disguised as a PDF file, taking advantage of Windows’ default behaviour of hiding the extension from file names to disguise the real .EXE extension. It could be contained in an Email which claims to have any of the following. (this is by no means an exhaustive list).
- A Payslip
- A Voicemail
- A Fax Message or Report
- A Delivery Document
- A Good or Services Order
- A Payment Receipt
- A Curriculum Vitae
- An “E” Gift Card
- A “personal” reply from a Forum Discussion
- A request for Quotation
- A Resume
- An Office Document with an embedded macro in it.
This macro is written in Visual Basic and once the document is opened it will download the malware from the WWW directly to the user’s machine. If you open a word document and get a message the same or similar to the below message you should be VERY suspicious about it and it would be best to contact your IT provider.
Right-Click to Search Google

What does it do?
When first run, the payload installs itself in the user profile folder and adds a setting to the computer that causes it to run on startup. It then attempts to contact one of several designated command and control servers on the Internet; once connected, the server generates an encryption code and sends that back to the infected computer.
Whichever form it comes in, once the payload executes, it may attempt to send an email to all contacts in your Outlook contact list with the infection in it. Then it encrypts files across local hard drives and mapped network drives. Once completed, the payload displays a message informing the user that files have been encrypted, and demands a payment through an anonymous pre-paid cash voucher. Payment of the ransom allows the user to download the decryption program, which is pre-loaded with the user’s private key.
YOU CANNOT DECRYPT YOUR DATA, SO UNLESS YOU HAVE A BACKUP, YOU EITHER PAY UP OR YOUR DATA IS GONE.
We need to bring this Virus / Ransomware to your attention again. Please read on.
PLEASE, PLEASE, PLEASE, relay to your staff how UNSAFE it is to open ANY document you are not expecting, even if it says it comes from a known source.
If activated on your system, CryptoLocker and all its variants will encrypt ALL common files that the users workstation has access to, this includes:-
- MS Office documents: .DOC, XLS etc, etc
- PDF Files
- Image files: .JPG, .TIF, CAD, etc, etc
It does this very fast, we have seen it encrypt approx. 110,000 files in under 20 minutes. It is hit and miss if your Firewall, Antivirus, User Policy Restrictions or Email filtering software will filter out the infection. New Variants of this virus are written all the time and some of the variants seem to get caught and some do not.
The following are examples of some of the Emails used to deliver the Virus.
The most recent was the below Email: Yesterday 30/06/2015
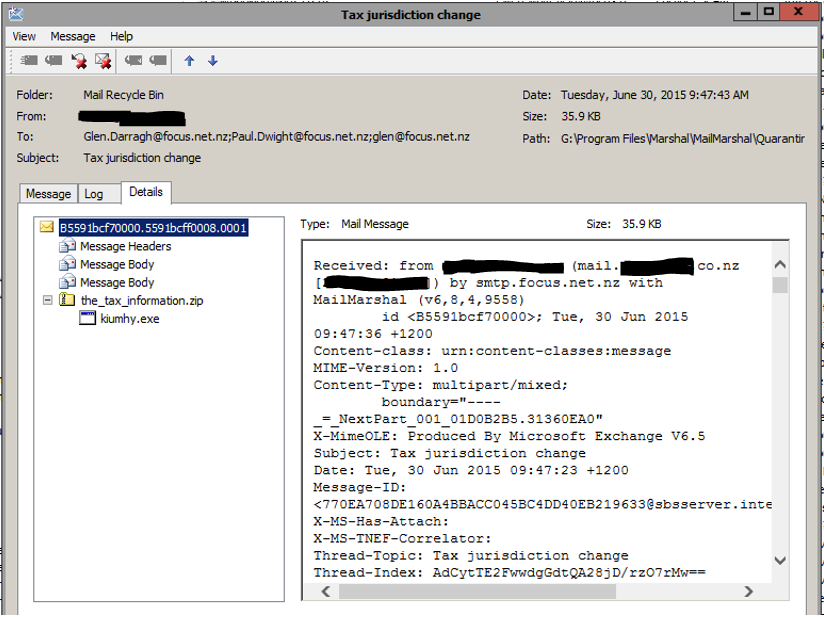
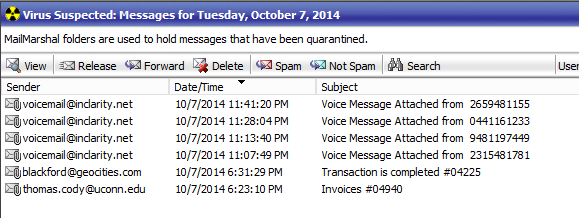
You will still find these older infection types also doing the rounds…
Kia Ora ,
Kindly find attached the Payment copy that was transferred to your account and let us know when the shipment will commence.
Margaret C. Sykes
Sales/GM of Export
King- Stone Trading Limited | 105 Hanover Street | PO Box 5743 | Dunedin | New Zealand
Phone: +64 3 471 8730 Facsimile: 64 3 430 8771
Skype: mcsykes.nz101
You will be DOUBLY at risk of this virus if your staff have access to their WEB based email such as Gmail from a work computer because it can infect in the same way from this source also.
What are the Signs of an infection?
- You suddenly cannot open files that you normally can access
- You look in your Data drive and see a file called for example: “filename.docx.encrypted”
- You look in a data directory and see these files:

- You look in your Data drive and see a file with a name similar to: “decryption_instructions.html”
- You go to open a file you know you have created, but it is missing
- You find yourself unable to open any of your data files.
- Your Accounting or Payroll package errors when trying to run reports.
What do you do if you think you are infected?
- If the Computer has a ransom message on its screen, TURN IT OFF IMMEDIATELY at the wall. Then call your IT provider.
- If you have mistakenly opened an email attachment and are unsure, TURN your computer OFF IMMEDIATELY at the wall. Then call your IT provider.
- If you have any signs of the above signs of infection but are unsure what computer is infected, get ALL USERS to shut down their computers and call your IT provider immediately..
What MUST you be doing now?
If you are a Focus client with a monitoring plan, Focus will be checking the backups each morning. If you are not then this task is completely up to YOU.
If you do get infected with this virus and you have GOOD BACKUPS, there is still a significant amount of time required to put things right. Backup files can be encrypted too, make sure your backup routine is right by talking to your IT provider.
If you are unsure or have any queries you should call your IT Provider. It’s much better to try to help prevent this than infection than to have to tidy up afterwards!
- You must make sure your staff are aware about the risk of browsing unknown webs sites or opening ANY email with an attached file.
- You MUST be checking your backups. If you are running Shadow Protect or Veeam and your backups are all valid then you only stand to lose a minimum amount of data. If you are running a nightly tape backup you will lose any data created since that last tape backup.






